Amazing Tips About How To Prevent Syn Flood
Block the most common attacks.
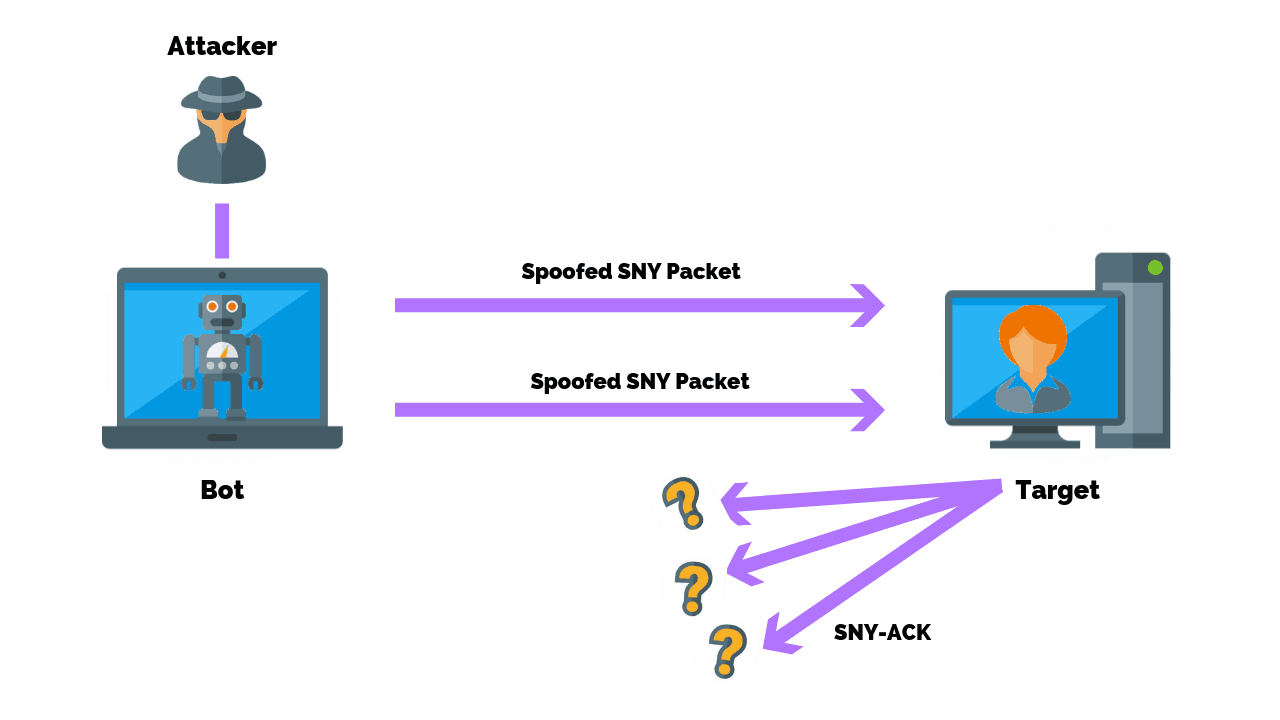
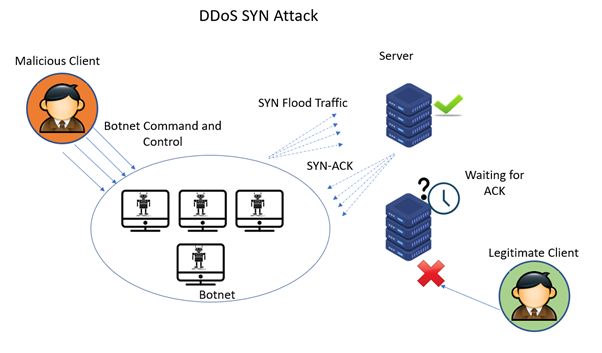
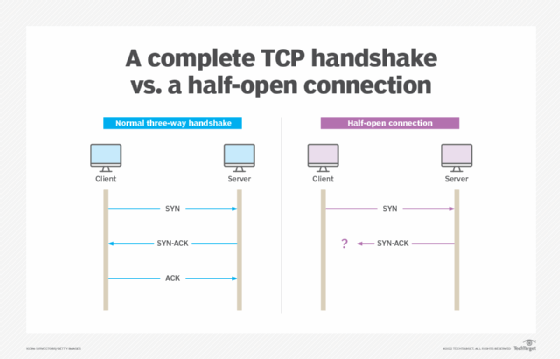
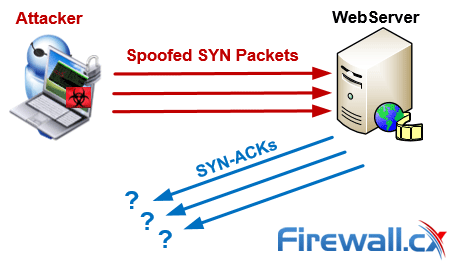
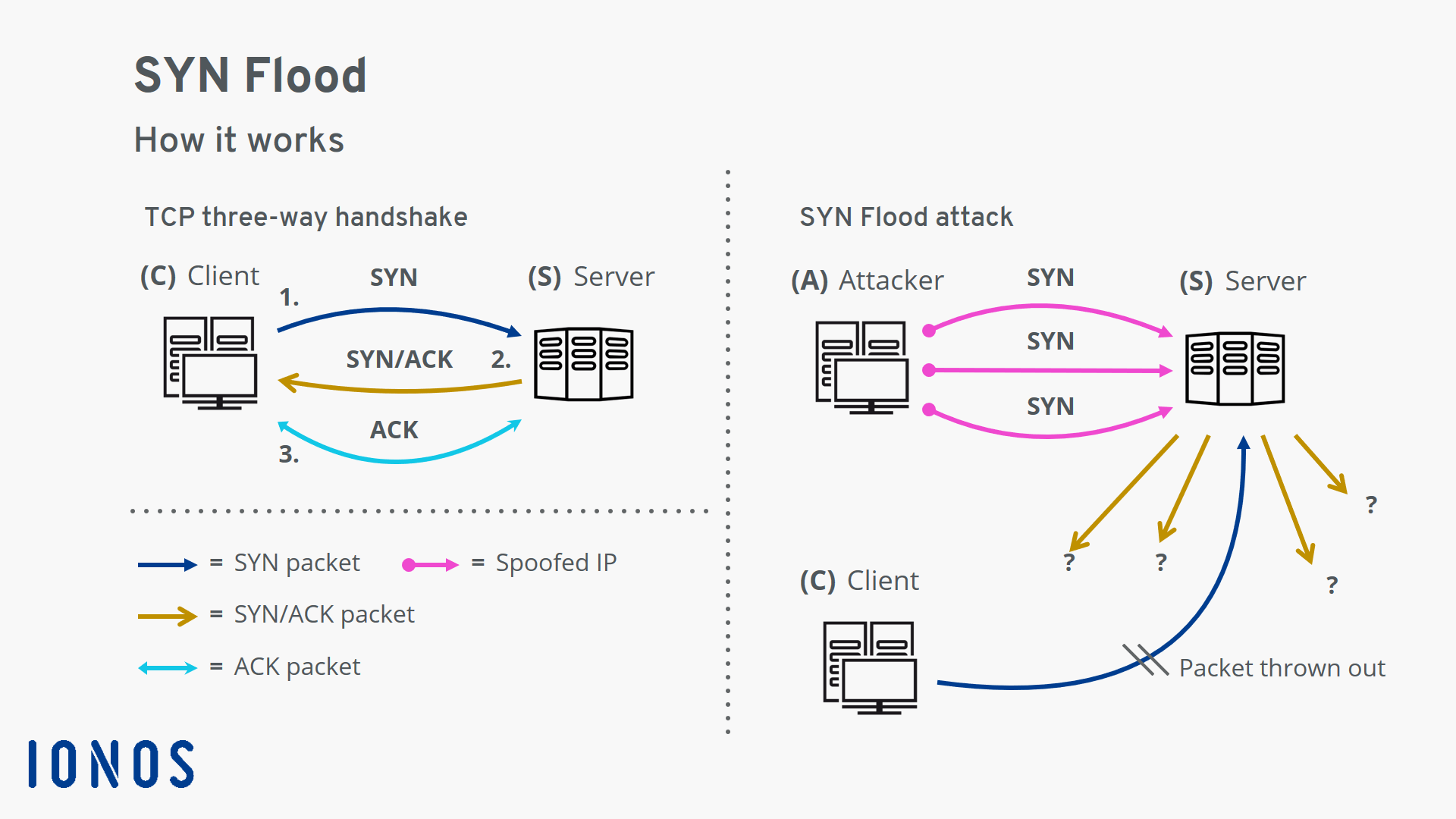
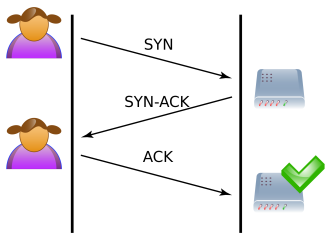
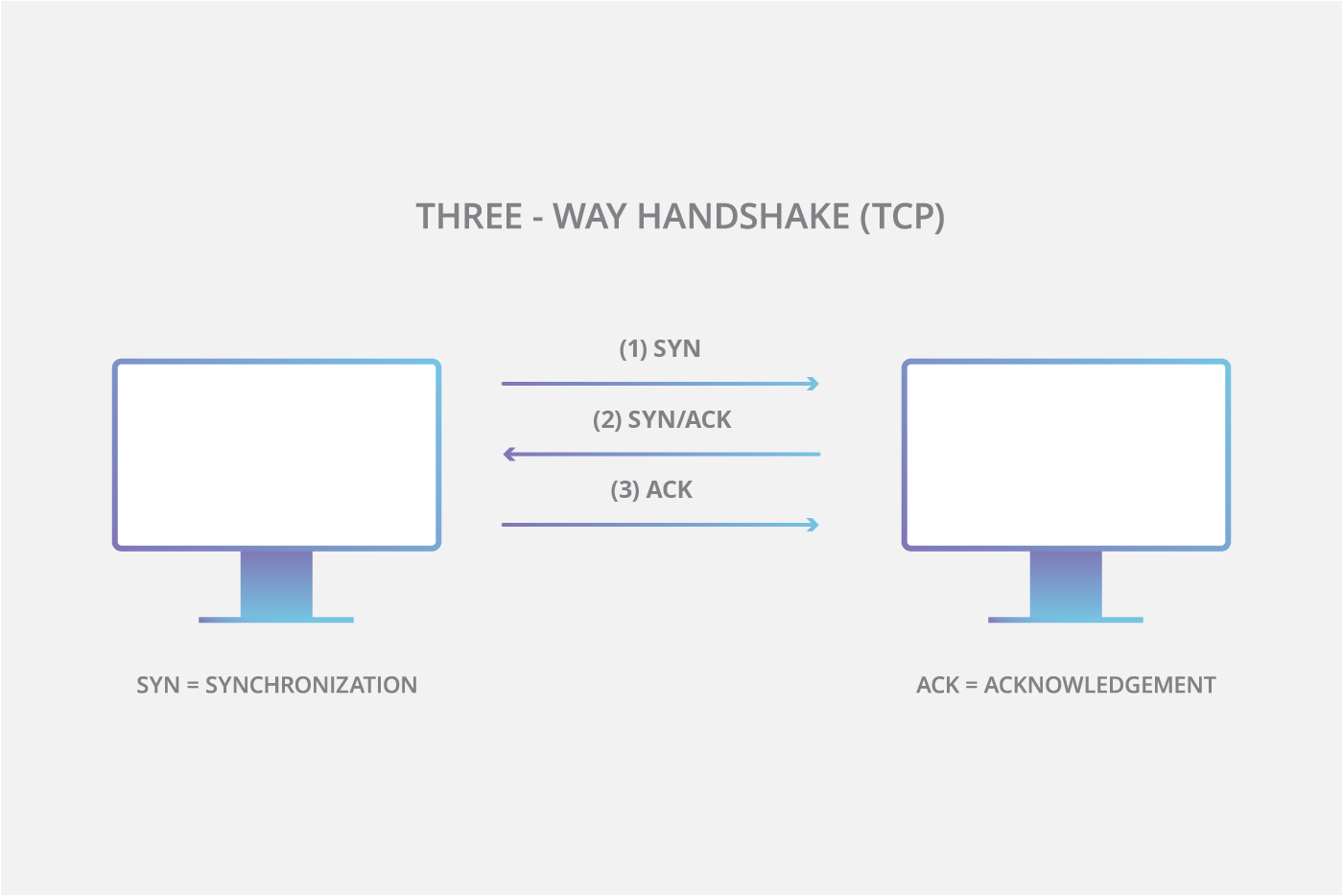
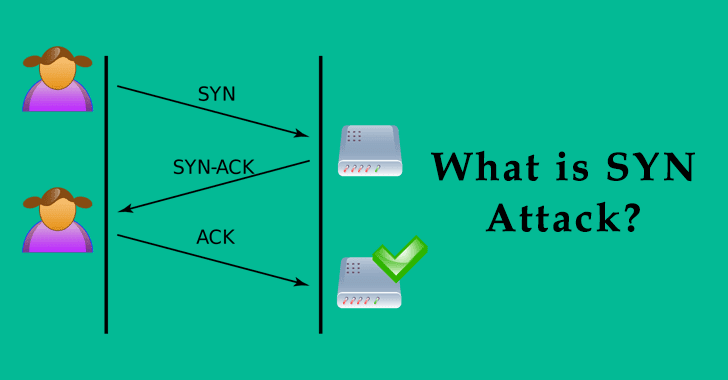
How to prevent syn flood. This is the most effective method of defending from syn flood attack. The attack is caused by one of the internal. There are several ways to mitigate syn flood attacks, including the following techniques:
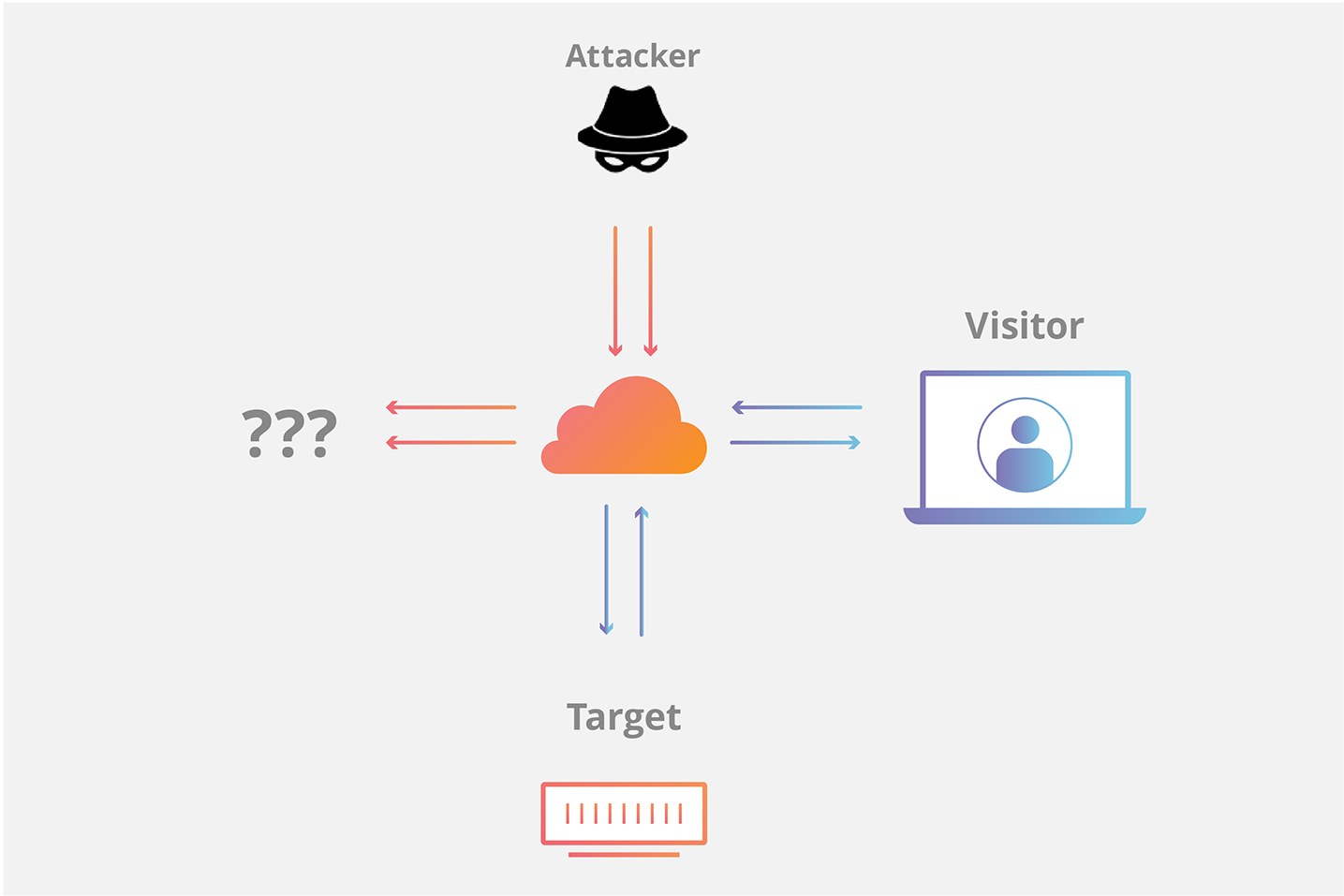
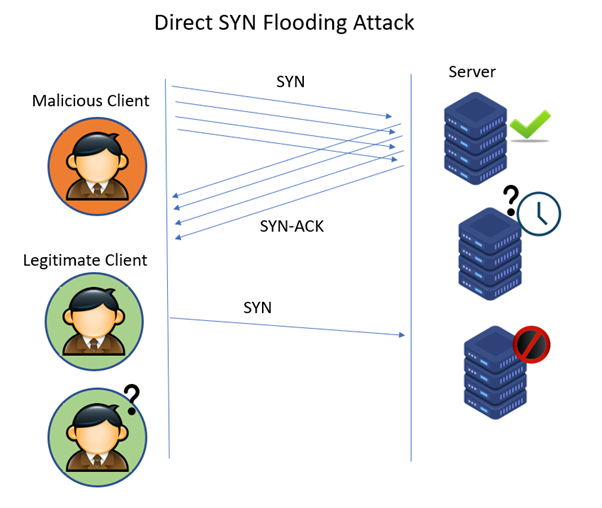
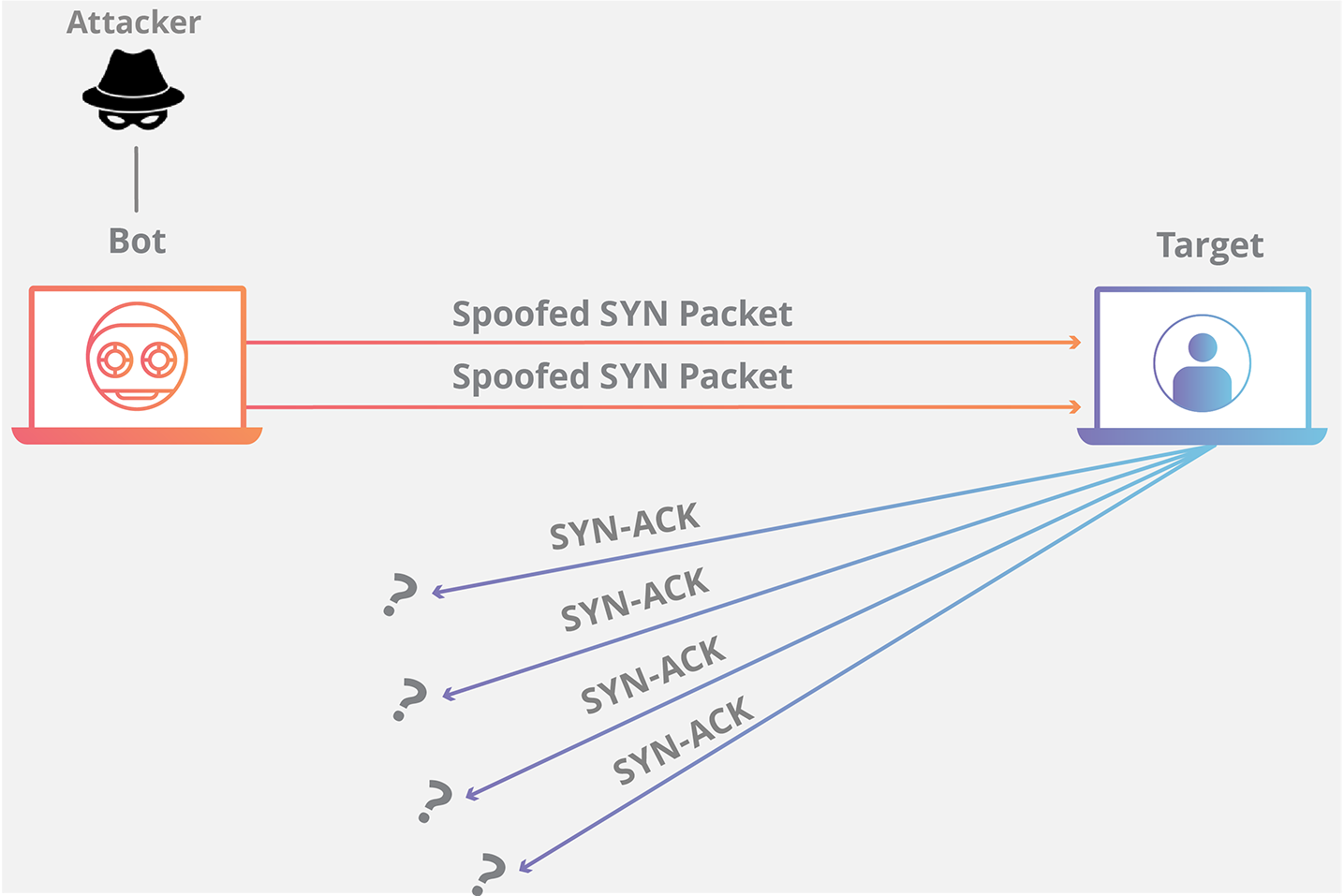
The number of syn requests that can be sent to a server at any one time is limited. Create a new virtual machine called kali linux and give it 1gb ram and set the network adapter to host only. Typically there is a loss of network connectivity and services because the bandwidth of the victim network is consumed.
Hostpalace vps's usually come with the empty configuration: By flooding a target with syn packets. • using syn cookies this is the most effective method of defending from syn flood attack.
In that os version, network administrators can. Syn flooding attack protection of tcp/ip (synattackprotect) for windows servers was added as an optional security measure in windows 2000. How to prevent syn flood attack?
We try to configuring connection limits and timeouts, for.